Email breaches struck 78% of organisations worldwide in the past year, costing an average US$217,000 per incident to remediate, with Australian businesses facing a 48% uptick in attacks this year.
Barracuda's newly released Email Security Breach Report surveyed 2,000 IT security decision-makers across nine countries and found 78% experienced an email security breach between April 2024 and May 2025, with 71% of those victims also getting hit with ransomware.
Organisations taking over two hours to detect and contain an email breach were substantially more likely to face ransomware, with 64% of ransomware victims requiring extended remediation time.
Average recovery costs hit $217,068 per breach, with smaller firms taking the worst beating.
Companies with 50 to 100 employees paid $1,946 per employee to recover versus $243 per head for organisations with 1,000-2,000 staff.
Detection speed matters: 58% of victims unaffected by ransomware detected breaches within an hour, compared to just 49% of those who also faced ransomware attacks.
Inundated down under
Australian organisations have been hit harder than most, with claimed data breaches jumping 48% in 2025.
Cyber researchers have recorded 71 breaches through to 3 October this year, up from 48 in the same period last year and already exceeding the 66 breaches recorded for all of 2024. About 50 of this year's breaches were claimed by ransomware groups.
The Australian Signals Directorate responded to over 1,200 cyber security incidents in 2024-25, an 11% increase, while receiving 84,700 cybercrime reports - one every six minutes.
Average self-reported costs for small businesses rose 14% to $56,600, whilst costs for individuals climbed 8% to $33,000.
The Office of the Australian Information Commissioner received 595 data breach notifications between July and December 2024, marking a 15% increase and the highest annual total since the Notifiable Data Breaches scheme commenced in 2018.
Attack methods
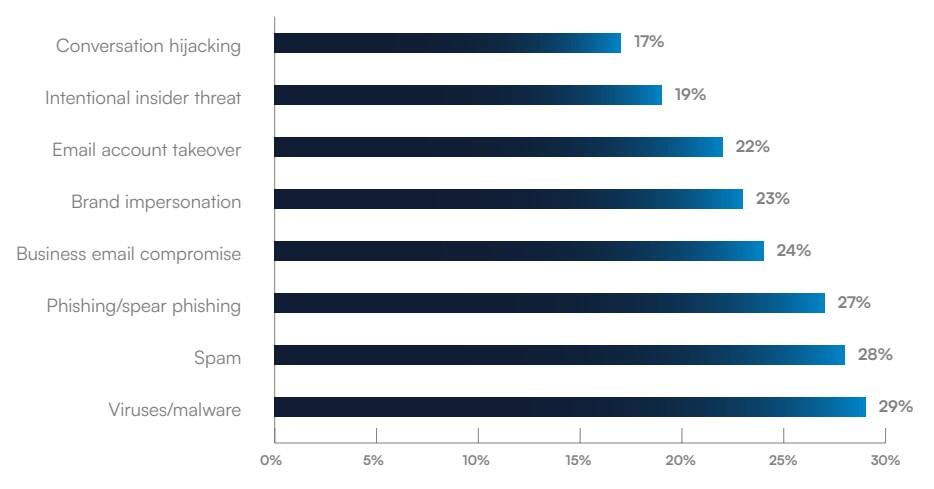
Worldwide, phishing and spear phishing topped the list, compromising 27% of breach victims, while business emails compromised 24% and account takeovers affected 22%.
The Barracuda survey found 47% of respondents cited advanced evasion techniques as the primary obstacle to rapid incident response.
Some 44% of organisations lack automated incident response capabilities, forcing security teams into manual processes.
A further 40% reported skilled personnel shortages, with this gap widening to 44% amongst organisations that fell victim to both email breaches and ransomware.
And about 46% of companies said employees assume security tools will protect them regardless of their actions.
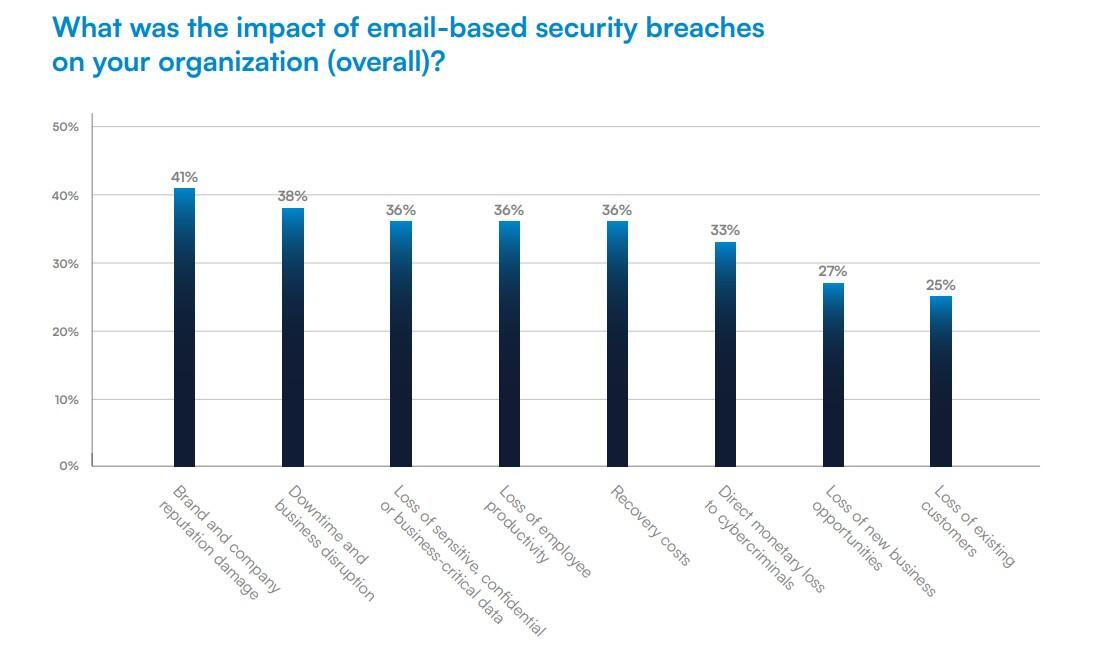
Brand damage topped the consequence list at 41%, followed by operational disruption at 38%.
Recent incidents:
- Seattle-based F5 disclosed on 15 October that nation-state actors maintained long-term access to its systems, stealing BIG-IP source code and vulnerability information. The company's stock dropped 10%, wiping nearly US$2 billion off its market cap.
- The Scattered Lapsus$ Hunters collective leaked personal data from 5.7 million Qantas customers on 11 October after a ransom deadline expired.
- Microsoft released an emergency patch on 23 October for CVE-2025-59287, a critical Windows Server Update Service vulnerability under active exploitation.
Supply chain exposure
Third-party compromises averaged $4.91 million in recovery costs according to IBM's 2025 report - the highest of any breach type.
Barracuda recommends automated incident response tools, multifactor authentication deployment, AI-powered detection systems, and employee training programmes.
Organisations that detect breaches within the first hour and respond immediately reduce their ransomware exposure substantially.
Any delays give attackers the runway they need to encrypt systems, exfiltrate data, and establish persistence across networks.



